States with a Cyber Civilian Corps.
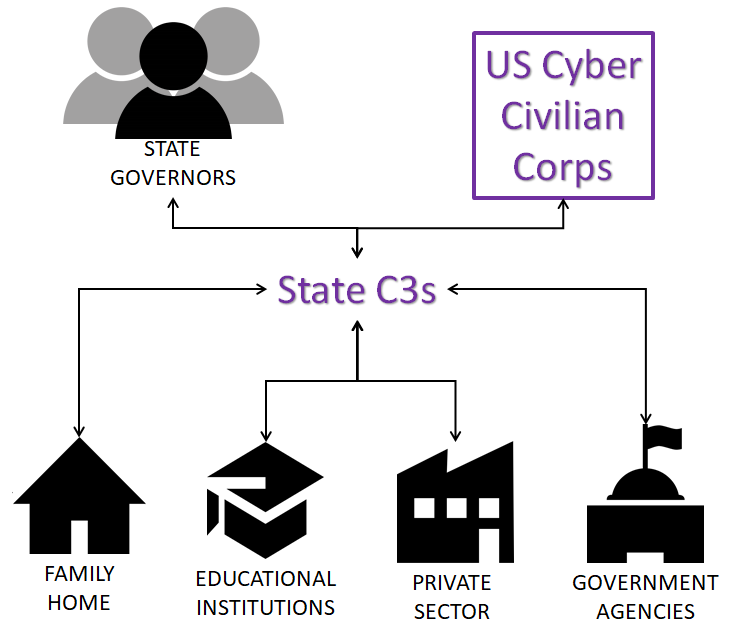
Many states have seen the need and are already funding their own Cyber Civilian Corps (C3).
- Indiana
- Michigan
- Minnesota
- Ohio
- District of Columbia
Defending our nation's and states' critical infrastructure is not solved with a whole of government approach; it requires a whole of nation.
We must increase our nation's cyber resiliency, share our cyber intelligence, and decrease the attack vectors used by nation states, VEOs, criminals, and hackers.
Our Four Key Pillars:
Educate
Educating on how cyberspace operates, its connections to the phyiscal world and how it is being weaponized and used against us is how we build our cyber resiliency. Our members work to educate our citizens in the aspects of cyber security and information operations. Investing in people over platforms is our greatest return.
“Education is the passport to the future, for tomorrow belongs to those who prepare for it today.” – Malcolm X
Share
Sharing information, knowledge, and experience is a force multiplier. We have built multiple communication channels to security share information and knowledge about current and potential cyber attacks.
“Share your knowledge. It is a way to achieve immortality.” ― Dalai Lama XIV
Support
Supporting the members of each state's Cyber Civilian Corps is our third pillar. Finding the necessary resources to support a given state's cyber civilian corps ensure they are able to perform their functions. It is our duty and obligation to find the means to ensure members maintain a high state of readiness to defend cyber assets.
Defend
Defending against and recovering from a cyber attack can be and almost always are at great cost. Not all entities have the capabilities or capacity to recover from a cyber attack. Our members work in a volunteer status to reduce recovery times.
Many states have seen the need and are already funding their own Cyber Civilian Corps (C3).

Our Struture and Relationships
In building the The United States Cyber Civilian Corps structure, several existing public private partnership (P3) frameworks and structures were leveraged. There were three main P3 organizations which influenced the United States C3 organization: the Civil Air Patrol, volunteer firefighters, and the Minnesota FBI Infragard's Public and Private Coordination and Action Team (P2CAT).
It is an honor to serve.

President
Phasellus eget enim eu lectus faucibus vestibulum. Suspendisse sodales pellentesque elementum.

Vice President
Phasellus eget enim eu lectus faucibus vestibulum. Suspendisse sodales pellentesque elementum.

Secretary
Phasellus eget enim eu lectus faucibus vestibulum. Suspendisse sodales pellentesque elementum.

Treasurer
Phasellus eget enim eu lectus faucibus vestibulum. Suspendisse sodales pellentesque elementum.
The United States Cyber Civilian Corps adheres to the National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework (NICE Framework). This framework is published by the National Institute of Standards and Technology (NIST) in NIST Special Publication 800-181. It is a nationally focused resource that establishes a taxonomy and common lexicon to describe cybersecurity work, and workers, regardless of where, or from whom, the work is performed. There are seven categories of common security functions.
Prior to assisting in any cyber defensive oprations, a C3 member must have the specific knowledge, skills, and abilities (KSAs) to perform tasks within the requested work role. This is required for two reasons. First, it instills confidence in those who are requesting help. And second, being in a voluneer status, shows due diligence that a C3 member is qualified for a given work role.
Analyze - Performs highly-specialized review and evaluation of incoming cybersecurity information to determine its usefulness for intelligence.
Collect and Operate - Provides specialized denial and deception operations and collection of cybersecurity information that may be used to develop intelligence.
Investigate - Investigates cybersecurity events or crimes related to information technology (IT) systems, entworks,a nd digital evidence.
Operate and Maintain - Provides the support, administration, and maintenance necessary to ensure effective and efficient information technology (IT) system performance and security.
Oversee and Govern - Provides leadership, management, direction, or development and advocacy so the organization may effectively conduct cybersecurity work.
Protect and Defend - Identifies, analyzes, and mitigates threats to internal information technology (IT) systems and/or networks.
Securely Provision - Conceptualizes, designs, procures, and/or builds security information technology (IT) systems, with responsibility for aspsects of system and/or network development.
Lets get in touch. Send us a message:
DAYTON MN 55327-9650
Phone: +1 (612) 000-0000
Email: @cyberciviliancorps.us